ENCRYPTION ACROSS THE OSI STACK
LAYERED NETWORK ENCRYPTION
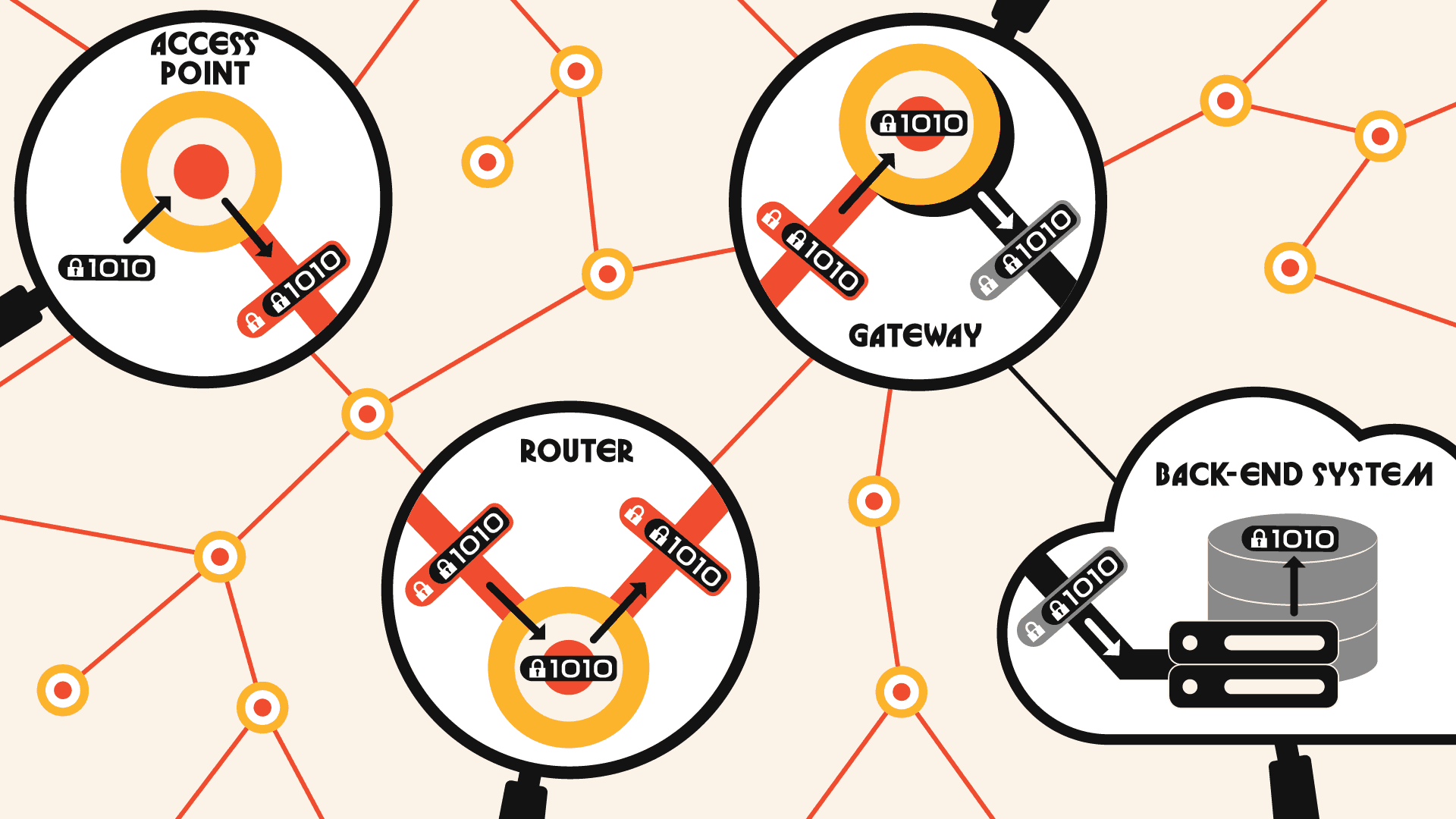
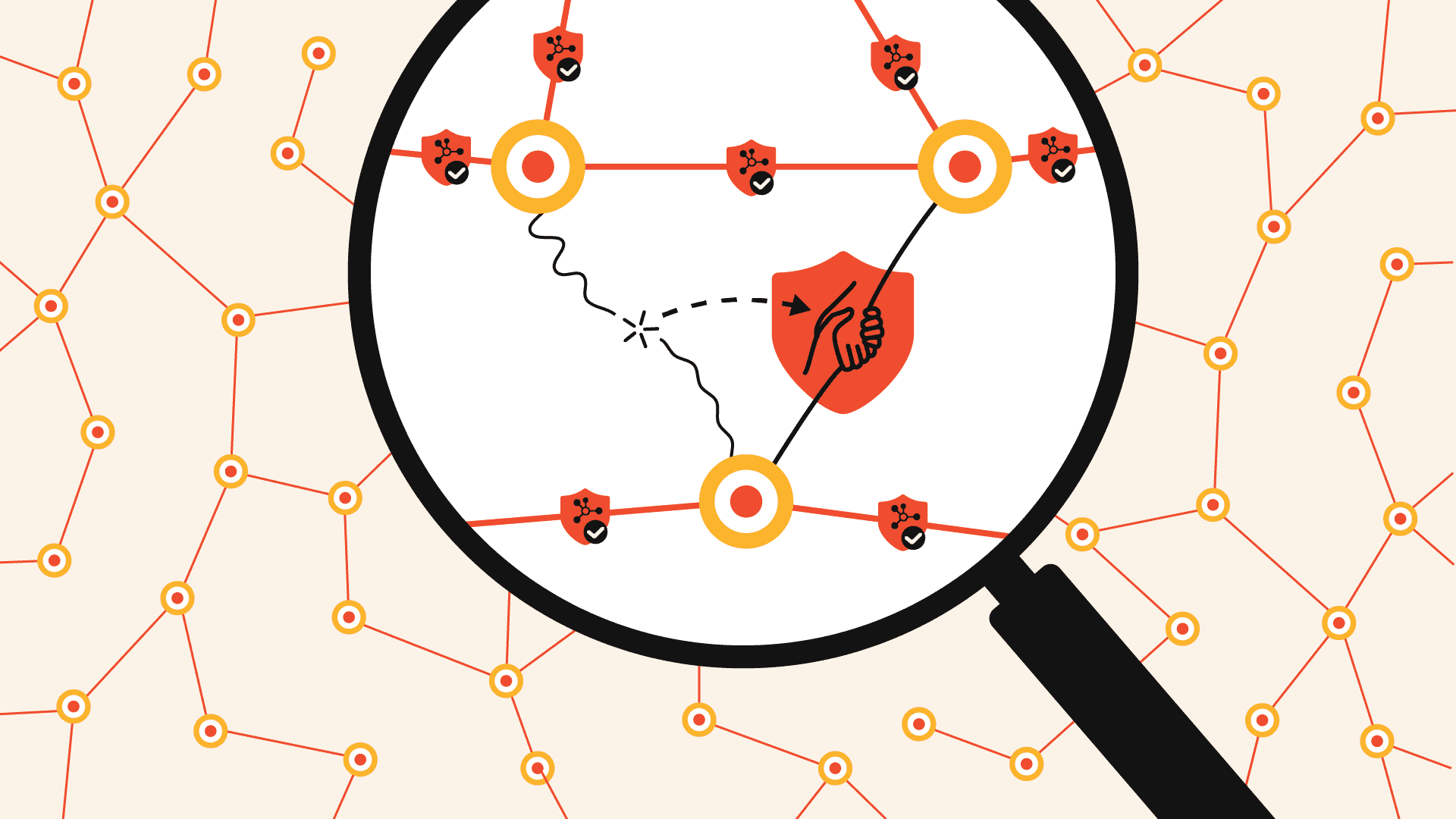
HOP-TO-HOP ENCRYPTION
Each node can only decrypt the data it needs to forward
Data is never visible in clear text beyond the current hop
The compromise of a single device does not expose the full message path
This model provides message protection without requiring end-to-end key sharing between every possible device pair.
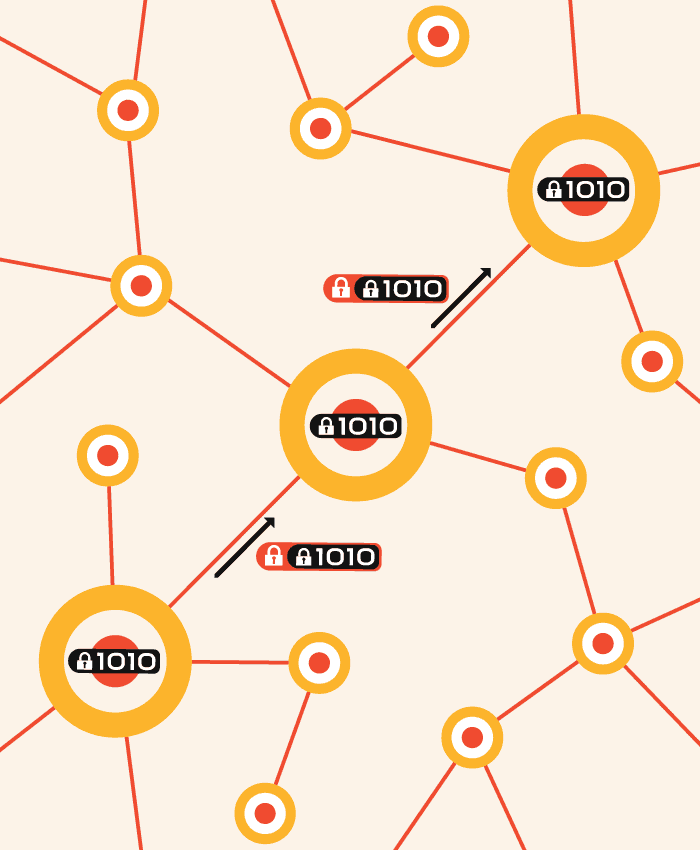
END-TO-END ENCRYPTION
Shared Mesh Networks. No problem.